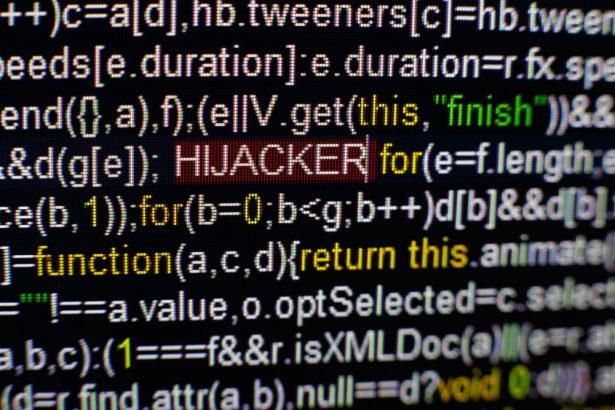
Giggle Pop-Up Scam: A Malicious Virus Threat
Pop-up scams have become increasingly prevalent, preying on unsuspecting users. These scams often masquerade as legitimate notifications, tricking individuals into disclosing personal information or downloading harmful software. As cybercriminals continually…
SwiftSeek: A Threat to Your Online Experience
In the vast landscape of the internet, users must navigate numerous threats to their online safety and privacy. One such threat is SwiftSeek, a malicious browser extension that can severely…
Tech News
Cyber Threats
How To Guides
Watch It



Product Reviews
How to Install and Uninstall Firefox, Microsoft Edge, Google Chrome, and Opera
In an increasingly digital world, ensuring that your web browser is secure…
Supercharging Your PC: How to Set Up Multiple SSDs for Optimal Performance
So, you’ve been cruising through your digital life with a trusty old…
What is the “About This Image” Tool and How to Use It
In an era where misinformation spreads faster than you can say "Clickbait,"…
IT / Cybersecurity Best Practices
Giggle Pop-Up Scam: A Malicious Virus Threat
Pop-up scams have become increasingly prevalent, preying on unsuspecting users. These scams often masquerade as legitimate notifications, tricking individuals into…
SwiftSeek: A Threat to Your Online Experience
In the vast landscape of the internet, users must navigate numerous threats to their online safety and privacy. One such…
DarkDev Ransomware: The Malicious Threat
Ransomware is a form of malicious software designed to deny access to a system or data until a ransom is…
More Latest News
Ztax Ransomware: A Comprehensive Guide to Understanding, Detecting, and Removing This Cyber Threat
Ransomware is a type of malicious software (malware) that encrypts files on…
Protecting Your PC: Understanding and Removing VBS.Gaggle.D Trojan Malware
In the ever-evolving landscape of cybersecurity threats, Trojans remain among the most…
FORCE Ransomware: A Lurking Cyber Threat
In the ever-evolving landscape of cyber threats, ransomware continues to reign as…
TL-Ver 36.1.com Ads Malware: A Removal Guide
A new cyber menace known as the "Check-tl.ver-36-1.com" adware has emerged, causing…
EstateRansomware: The Threat to Your Digital Security, Exploiting CVE-2023-27532
Ransomware stands out as a particularly malicious form of malware. Its primary…
Guce.advertising.com Redirects Users to Unreliable Websites Containing Sponsored Ads
If you have an AOL email account, you probably encountered a Guce…
Bitcoin Email Virus: A Comprehensive Guide
In the digital age, cyber threats continue to evolve, with malware posing…
NanoBoost: Understanding and Removing the Adware Threat
In the digital landscape, where convenience and connectivity thrive, cyber threats continue…