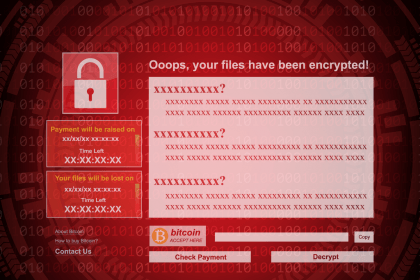
Imploder Ransomware: A Growing Threat to Your Files
Imploder is a newly discovered ransomware that has raised concern among cybersecurity…
Pro Video Downloader: A Dangerous Adware Threat
Pro Video Downloader is an extension promoted as a convenient tool for…
ViT Ransomware: How to Detect, Remove, and Protect Against This Dangerous Threat
ViT ransomware, part of the notorious Xorist family, is a highly destructive…
Revive Ransomware: How to Remove It and Prevent Future Infections
Ransomware remains one of the most alarming forms of malware, targeting both…
MAGA Ransomware: A Comprehensive Guide to Detection, Removal, and Prevention
Ransomware attacks are among the most devastating forms of cyber threats, capable…
Heur.AdvML.b: Understanding the Threat and How to Remove It
Heur.AdvML.b is a heuristic detection name assigned by antivirus software to flag…
WIN32/Offercore.b: What It Is, How It Works, and How to Remove It Completely
WIN32/Offercore.b is a potentially unwanted program (PUP) that operates with malicious capabilities,…
Claim Strategic Bitcoin Reserve Scam: A Comprehensive Guide to Avoid and Remove This Threat
The cryptocurrency market, while brimming with opportunities, is increasingly becoming a playground…
Rockstar 2FA PhaaS Toolkit: A New Era of Sophisticated Phishing Threats and How to Remove It
The Rockstar 2FA PhaaS (Phishing-as-a-Service) toolkit represents a particularly alarming threat, capable…
“Viruses Have Been Detected On Your Phone” Scam: A Complete Removal Guide
The "Viruses Have Been Detected On Your Phone" scam is a manipulative…