NonEuclid Remote Access Trojan: Analysis and Removal Guide
The NonEuclid Remote Access Trojan (RAT) is a sophisticated piece of malware…
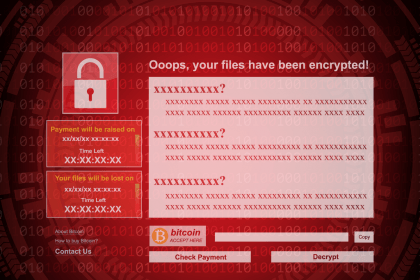
Kixtixcy Ransomware: Analysis and Removal Guide
Kixtixcy ransomware, a new strain of the notorious Dharma ransomware family, is…
Fyallusad[.]top: A Gateway to Online Scams and Threats
Threats like fyallusadtop are becoming increasingly sophisticated in luring unsuspecting users. Fyallusadtop…
IOCONTROL Malware: A Serious Threat to Critical Infrastructure
The cyber threat landscape has grown increasingly complex, with state-sponsored groups targeting…
X101 Ransomware: Understanding, Removal, and Prevention
Ransomware is a type of malicious software designed to block access to…
Emmenhtal Malware: Detection, Removal, and Prevention
Emmenhtal is a particularly insidious malware threat that poses significant risks to…
RevC2 Malware: A Comprehensive Guide to Detection, Removal, and Prevention
RevC2 is a sophisticated backdoor malware strain primarily distributed through the Venom…
UEVRBackend.dll: A Potential Malware Threat
What Is UEVRBackend.dll? UEVRBackend.dll is a dynamic link library (DLL) associated with…