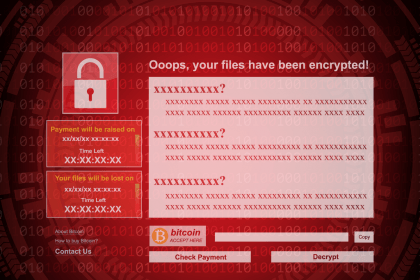
Understanding and Removing The Bully Ransomware
Ransomware is a notorious form of malware that encrypts files on a…
FoxTro Ransomware: Actions, Consequences, and Removal Guide
Ransomware remains one of the most devastating cyber threats facing individuals and…
MoneyIsTime Ransomware: Dealing with File Encrypting Malware
Ransomware is a type of malicious software designed to deny access to…
Hawk Eye Ransomware: A Deep Dive into the Insidious Ransomware Threat
Ransomware is a type of malicious software designed to block access to…
Zola Ransomware: A Comprehensive Guide to Threat and Removal
Ransomware is a form of malicious software designed to block access to…
EstateRansomware: The Threat to Your Digital Security, Exploiting CVE-2023-27532
Ransomware stands out as a particularly malicious form of malware. Its primary…
Joker Chaos Ransomware: Actions, Consequences, and Removal
Ransomware continues to be a significant concern for individuals and organizations alike.…
Jinwooks Ransomware: A Comprehensive Guide to Detection, Removal, and Prevention
Ransomware continues to be a formidable adversary in the cybersecurity landscape, with…
Lord Bomani Ransomware: A Comprehensive Guide
Ransomware remains one of the most pervasive and destructive forms of malware.…
Boost Ransomware: A Growing Cyber Threat
Ransomware continues to be a prevalent and damaging menace. Among the latest…