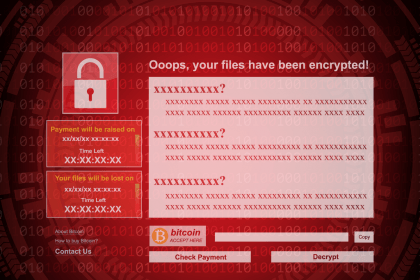
LucKY_Gh0$t Ransomware: What You Need to Know
The LucKY_Gh0$t ransomware is a dangerous threat that can severely impact both…
Aptlock Ransomware: Understanding, Removing, and Preventing Future Infections
Aptlock ransomware is a notorious malware threat designed to encrypt files on…
FunkLocker (FunkSec) Ransomware: A Detailed Overview and Removal Guide
FunkLocker, also known as FunkSec, is a ransomware-type malware that encrypts files…
Contacto Ransomware: A Detailed Overview, Removal Guide, and Prevention Tips
Ransomware is a malicious type of software that locks users out of…
YE1337 Ransomware: Overview, Removal Guide, and Prevention Tips
Ransomware attacks are among the most severe and financially damaging types of…
Nitrogen Ransomware
Nitrogen ransomware is a sophisticated and dangerous malware designed to encrypt files…
Bbuild Ransomware Threat and How to Protect Your System
Ransomware attacks continue to pose a significant threat to individuals and organizations…
RdpLocker Ransomware: Understanding and Removing the Threat
What is RdpLocker? RdpLocker is a type of ransomware designed to encrypt…
Kixtixcy Ransomware: Analysis and Removal Guide
Kixtixcy ransomware, a new strain of the notorious Dharma ransomware family, is…
Teaneck.exe Trojan: A Dangerous Malware Threat
Trojans are a type of malicious software designed to deceive users into…