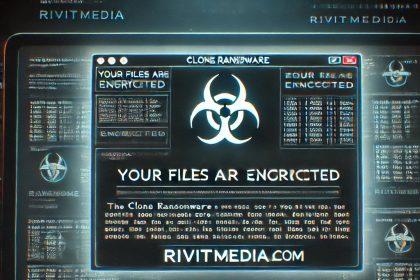
Clone Ransomware: Analysis, Removal, and Prevention
Clone ransomware, a member of the notorious Dharma ransomware family, has been…
Vulcan Ransomware: A Threat Analysis and Removal Guide
What is Vulcan Ransomware? Vulcan is a ransomware variant designed to encrypt…
.Held Ransomware: A Holiday Nightmare for 2024 and How to Remove It Safely
As the holiday season of 2024 unfolds, cybercriminals have rolled out their…
Adver Ransomware: A Comprehensive Guide on Threat Overview, Removal, and Prevention
Ransomware continues to be a significant threat to both individual users and…
Black Basta Ransomware Exploits New Social Engineering Tactics: A Growing Cybersecurity Threat
The Black Basta ransomware group, notorious for its persistence and adaptability, has…
Moonman/UwU Ransomware: A Comprehensive Guide to Understanding, Detecting, and Removing This Dangerous Threat
Ransomware is a malicious software designed to hold your files hostage by…
Arachna Ransomware: Understanding, Symptoms, Removal, and Prevention
Ransomware is a type of malicious software designed to block access to…
AnonWorld Ransomware: A Comprehensive Analysis and Removal Guide
Ransomware is a malicious type of software designed to encrypt files on…
BioBio Kasper Ransomware: A Guide to Detection, Removal, and Prevention
Ransomware is a dangerous and malicious form of malware that encrypts files…
Weaxor Ransomware: A Comprehensive Removal Guide
Ransomware is a type of malicious software that encrypts a victim's files,…