“Spotify Subscription Update” Email Scam: A Comprehensive Analysis and Removal Guide
The "Spotify Subscription Update" email scam is a phishing campaign aimed at…
SyncRemote Adware: Understanding the Threat and Protecting Your System
SyncRemote is a newly identified adware application belonging to the AdLoad malware…
What Is Unbosperismoles.co.in?
Unbosperismoles.co.in is a suspicious and potentially harmful domain associated with browser hijackers,…
CENUTIX Crypto Scam: Recognizing, Removing, and Preventing Future Attacks
Scams and fraudulent activities are becoming increasingly sophisticated, making it essential for…
Nanopicoen Browser Hijacker: Understanding the Threat and How to Remove It Effectively
In the world of cybersecurity, browser hijackers such as Nanopicoen are becoming…
Weisx App: A Dangerous Unwanted Application and How to Remove It
Threats such as unwanted applications continue to plague unsuspecting users. One such…
Ninja Browser: A Threat to Your Privacy and Security
Web browser users are drawn to applications promising enhanced privacy, faster downloads,…
F95.zone: A Deceptive Threat to Your Online Security
The digital landscape is rife with malicious entities posing threats to user…
Held Ransomware: Detection, Removal, and Prevention
Held ransomware, a member of the infamous Djvu family, is a malicious…
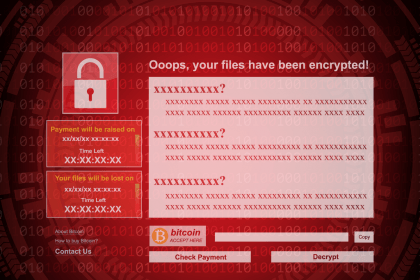
Kixtixcy Ransomware: Analysis and Removal Guide
Kixtixcy ransomware, a new strain of the notorious Dharma ransomware family, is…