Topads-site.com: What You Need to Know and How to Remove It
Topads-site.com is a suspicious domain associated with intrusive push notifications and misleading…
Fishbtrads.top
The internet is a boundless resource for information, entertainment, and convenience, but…
Downloading Pro Media Removal and Preventing Future Infections
Potentially Unwanted Programs (PUPs) continue to evolve as a significant cybersecurity concern…
Revive Ransomware: How to Remove It and Prevent Future Infections
Ransomware remains one of the most alarming forms of malware, targeting both…
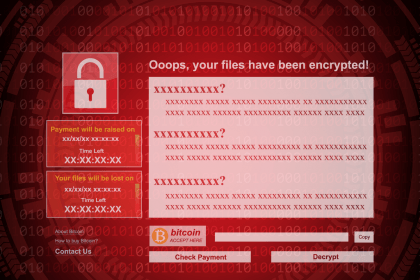
MAGA Ransomware: A Comprehensive Guide to Detection, Removal, and Prevention
Ransomware attacks are among the most devastating forms of cyber threats, capable…
Claim Strategic Bitcoin Reserve Scam: A Comprehensive Guide to Avoid and Remove This Threat
The cryptocurrency market, while brimming with opportunities, is increasingly becoming a playground…
Rockstar 2FA PhaaS Toolkit: A New Era of Sophisticated Phishing Threats and How to Remove It
The Rockstar 2FA PhaaS (Phishing-as-a-Service) toolkit represents a particularly alarming threat, capable…
“New Submission – Your Bitcoin Transfer Pending: Finalize It Today!” Scam: How to Protect Yourself from This Cryptocurrency Fraud
Cryptocurrency scams continue to rise, taking advantage of unsuspecting individuals with fraudulent…
Arachna Ransomware: Detailed Analysis, Removal Guide, and Prevention Tips
Ransomware attacks are among the most devastating cyber threats, and the Arachna…
Moonman/UwU Ransomware: A Comprehensive Guide to Understanding, Detecting, and Removing This Dangerous Threat
Ransomware is a malicious software designed to hold your files hostage by…