Search-thrill.com Browser Hijacker: How to Remove and Prevent Future Infections
What is Search-thrill.com? Search-thrill.com is a suspicious website, commonly categorized as a…
Capital One – Email Address Change Scam: How to Identify, Remove, and Protect Yourself
The "Capital One - Email Address Change" scam is a classic example…
FormatLocator Adware: Overview and Threat Assessment
FormatLocator is a malicious adware program that primarily targets Mac users, delivering…
GlobalHelper Adware Overview
GlobalHelper is a type of adware that infiltrates computers, primarily Macs, to…
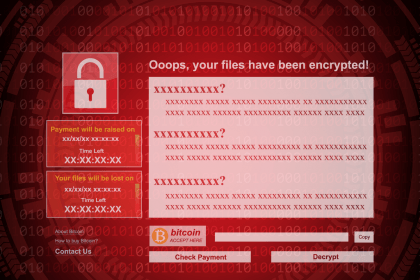
Aptlock Ransomware: Understanding, Removing, and Preventing Future Infections
Aptlock ransomware is a notorious malware threat designed to encrypt files on…
nfotofind.com: Removal and Prevention
Infotofind.com is a deceptive search engine linked to browser hijackers. These programs,…
Trojan:HTML/Redirector.GPAY!MTB – Understanding and Eliminating the Threat
Cybersecurity threats like Trojan:HTML/Redirector.GPAY!MTB are increasingly common, putting unsuspecting users at risk…
Blissfulluck.cfd: A Comprehensive Guide to Removal and Prevention
What Is Blissfulluck.cfd? Blissfulluck.cfd is a browser add-on that masquerades as a…
HSBC – Account Credited With An Inward Payment: Phishing Scam
Phishing scams have become increasingly sophisticated, with attackers continuously evolving their methods…