Ransomware is a notorious form of malware that encrypts files on a victim’s computer, rendering them inaccessible. Cybercriminals use this malicious software to demand a ransom in exchange for a decryption key that will restore the user’s access to their files. As the prevalence of ransomware attacks continues to grow, it is crucial for individuals and organizations to understand the specific threats they may encounter, including one such threat known as The Bully Ransomware.
The Bully Ransomware: Functionality and Threat
The Bully Ransomware operates by infiltrating a user’s system and executing a series of harmful actions. Typically, it gets installed through malicious email attachments, software downloads from untrustworthy sources, or by exploiting vulnerabilities in outdated software. Once The Bully Ransomware gains access, it begins to encrypt files, changing their original file extensions to ones that signal their compromised status. For example, files may be renamed with the extension .bully.
Upon installation, The Bully Ransomware can cause significant damage. It scans the infected system for various file types—such as documents, images, and videos—and encrypts them, making recovery impossible without the corresponding decryption key. The consequences of its presence include loss of access to important files, financial losses due to ransom payments, and potential exposure of sensitive personal information.
Ransom Note Overview
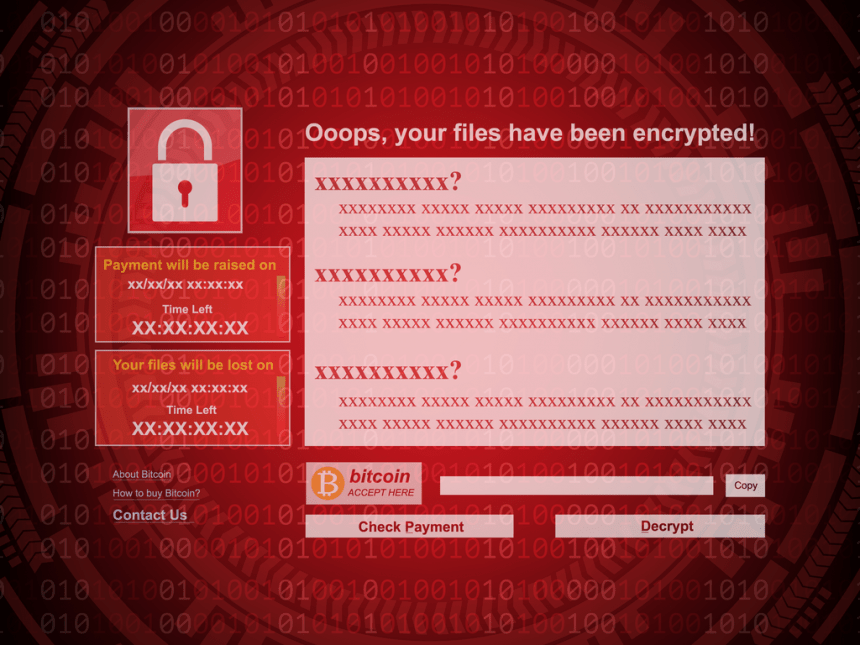
Once the encryption process is complete, The Bully Ransomware leaves a ransom note on the infected system. This note typically contains instructions on how to pay the ransom, often demanded in cryptocurrency to ensure anonymity for the attackers. The note may also threaten to permanently delete the decryption key if the ransom is not paid within a specified timeframe, instilling a sense of urgency in the victim.
The general purpose of The Bully Ransomware—and ransomware in general—is to extort money from victims by leveraging their fear of losing valuable data. Cybercriminals infiltrate systems using various methods, including phishing emails, malicious links, and software vulnerabilities. The threat poses significant risks not only to the integrity of the infected system but also to the individual whose personal and sensitive data may be compromised.
Symptoms of The Bully Ransomware Infection
Identifying an infection by The Bully Ransomware can be challenging, but certain symptoms may indicate its presence:
- Inability to access certain files or folders.
- Files appearing with unfamiliar extensions (e.g.,
.bully). - A ransom note appearing on the desktop or within encrypted folders.
- Unusual system behavior, such as slow performance or crashes.
Detection Names
Users can look out for specific detection names that indicate The Bully Ransomware may be present on their systems. Common detection names include:
- BullyRansom
- Ransom.Bully
- Ransom:Win32/Bully
Similar Threats
In addition to The Bully Ransomware, users should be aware of similar ransomware threats they may encounter, such as:
- Locky Ransomware
- Cerber Ransomware
- WannaCry Ransomware
Comprehensive Removal Guide
If you suspect that your system is infected with The Bully Ransomware, follow these steps to remove it:
Step 1: Disconnect from the Internet
- Immediately disconnect your computer from the internet to prevent the ransomware from communicating with its command server and to stop further file encryption.
Step 2: Enter Safe Mode
- Restart your computer.
- Press
F8(or the appropriate key for your system) during boot-up. - Select Safe Mode with Networking from the options.
Step 3: Identify the Ransomware Process
- Press
Ctrl + Shift + Escto open Task Manager. - Look for unfamiliar processes that are running. You may not be able to identify the ransomware easily, but if you see any suspicious applications, take note of them.
Step 4: Delete Ransomware Files
- Open File Explorer and navigate to the following locations:
C:\Program FilesC:\ProgramDataC:\Users\[Your Username]\AppData\LocalC:\Users\[Your Username]\AppData\Roaming
- Search for any files or folders associated with The Bully Ransomware and delete them.
Step 5: Use Antivirus/Anti-Malware Software
- Download a reputable antivirus or anti-malware tool (such as SpyHunter) if you haven’t already.
- Update the software to ensure it has the latest definitions.
- Perform a full system scan to detect and remove The Bully Ransomware and any other malware present.
Step 6: Restore Your Files (If Possible)
If you have backups of your files, you may restore them after ensuring that the ransomware is completely removed. Do not connect any external drives until you are sure the system is clean.
Step 7: Monitor Your System
After the removal process, monitor your system for any signs of re-infection or unusual behavior. Consider changing passwords for sensitive accounts as an additional precaution.
Preventing Future Infections
To prevent future infections from ransomware like The Bully Ransomware, consider these steps:
- Regular Backups: Regularly back up your files to an external hard drive or cloud storage. Ensure backups are not connected to your main system during an attack.
- Keep Software Updated: Regularly update your operating system and applications to patch vulnerabilities.
- Be Cautious with Emails: Avoid clicking on links or downloading attachments from unknown or suspicious emails.
- Use Reliable Security Software: Employ reputable antivirus and anti-malware software, such as SpyHunter, to scan your system regularly and provide real-time protection.
Promoting tools like SpyHunter can significantly enhance your security against ransomware and other malware threats. Download it and scan your computer for free to ensure a safe and secure environment.